Android and iOS represent the lion's share of the mobile operating system market, and while there's inherent risk with the use of any mobile device in the enterprise, Android presents a much bigger target for malware attacks and, in turn, corporate security issues.
With the massive growth of Android-powered devices in businesses over the past couple of years, companies need a strategy to minimize any risk the platform may pose, according to industry research firm J. Gold Associates.
"Even if you modify the look and feel of a messaging app, you may not know you've added a vulnerability," he said. "That's the problem with open code, you never know until you've tested it."
Conversely, Apple's iOS is much more restrictive with what developers can do and Apple doesn't release its source code. That means, generally, that iPhones [and iPads] are harder to jailbreak than Android phones, Gold said, "because Apple puts all kinds of restrictions on them and they'll check you every now and then. And, if they find a phone is jailbroken, they'll shut you down.
"And, because Apple controls the hardware and the software, they have the ability to impose tighter security," Gold added.
In some ways, Android has also suffered from its success.
Android and iOS now account for 94% of the mobile operating system market worldwide, according to Forrester Research's just-released "Mobile, Smartphone, And Tablet Forecast, 2017 To 2022." Android is the dominant platform for smartphones, capturing 73% of the market with more than 1.8 billion subscribers in 2016, according to Forrester.
Android is expected to maintain the lead this year, according to Forrester, with 74% market share, followed by Apple with 21% and Windows Phone with just 4%.
"The truth is, when Android gets attacked, it tends to be more vulnerable because there are more devises out there and more people also hear about it," Gold said. "Android also has a problem in that the latest version of Android OS is generally a small portion of the base of devices in the marketplace. So, when upgrades are issued, not everyone gets them. Whereas, when Apple upgrades, everyone gets it."
Additionally, as enterprises develop more of their own custom applications -- many of them mobile apps as part of a mobile-first strategy -- in-house developers are increasingly at risk of unwittingly using open-source code rife with vulnerabilities.
Applications today are rarely coded from scratch, particularly when software is created outside a company's development and operations units. Developers typically go to online libraries for open-source components -- chunks of code that act as building blocks -- to assemble custom mobile apps. Not only can chunks of code be modified, but they can natively contain vulnerabilities.
Mobile threat detections double
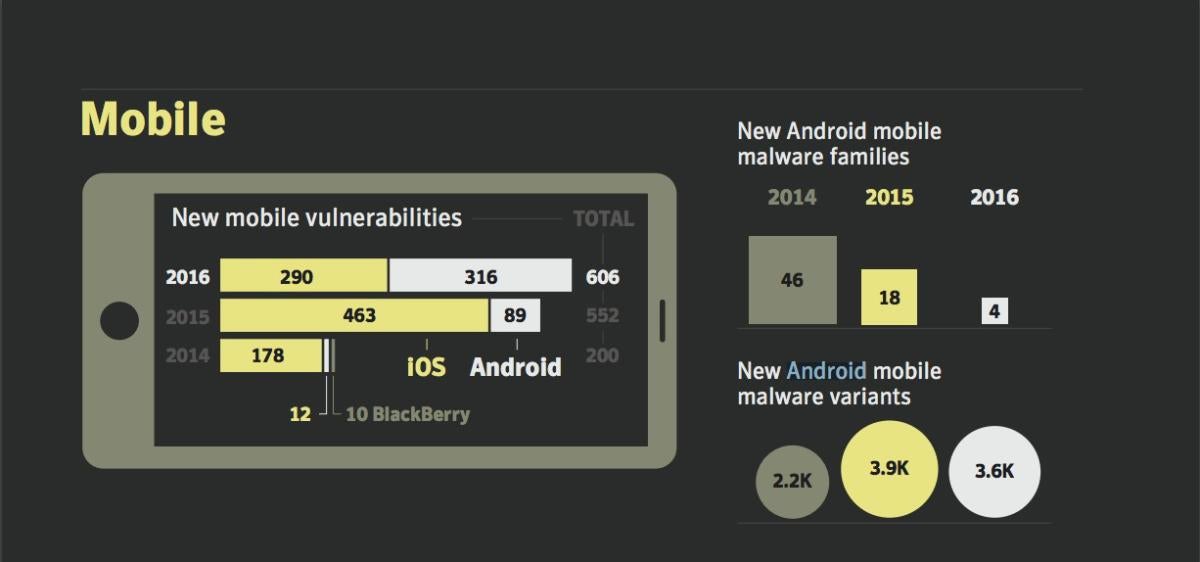
According to Symantec's Internet Security Threat Report issued in April, overall threat detections on mobile devices doubled last year, resulting in 18.4 million mobile malware detections. Similar threats were seen in 2015, according to Symantec, with 5% of all devices being targeted for infection in each of the past two years.According to Symantec, from 2014 through 2016 the level of iOS vulnerabilities remained fairly flat. And while new Android malware families dropped significantly, from 46 in 2014, to 18 in 2015 and just 4 in 2016, the OS remains the main focus for mobile attacks, Symantec noted.
The overall volume of malicious Android apps increased significantly in 2016, growing by 105%, but that was still smaller than in 2015, when the number of malicious apps increased by 152%.
Mobile malicious threats are grouped into "families," and "variants." Malware families are a collection of threats from the same or similar attack groups. In 2014, there were 277 malware families overall. That grew to 295 families in 2015 and 299 in 2016. So while the number of new families grew more slowly, the overall number of threats remained sizable.
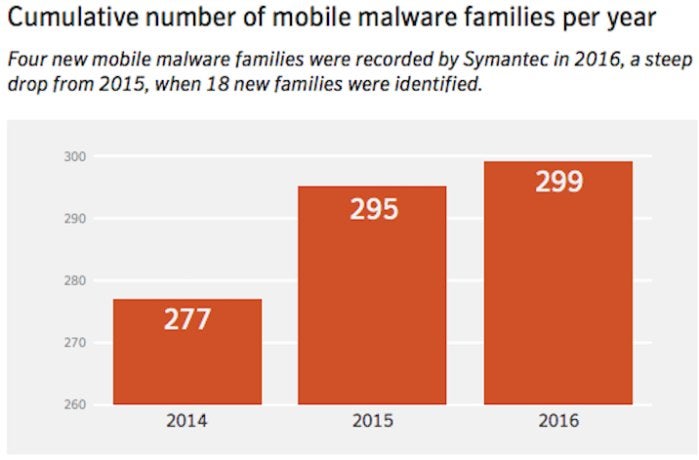
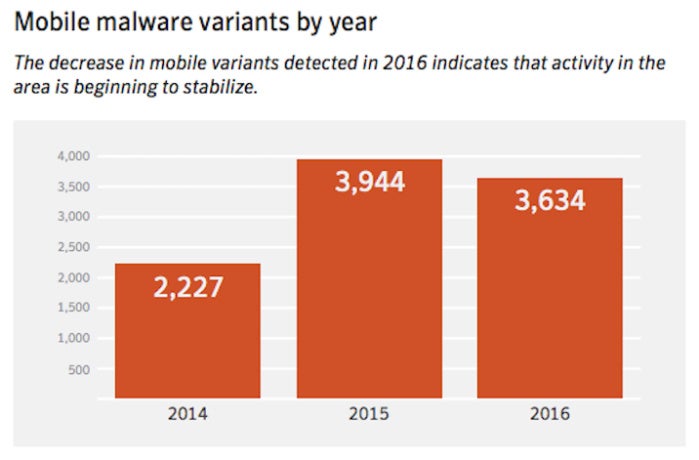
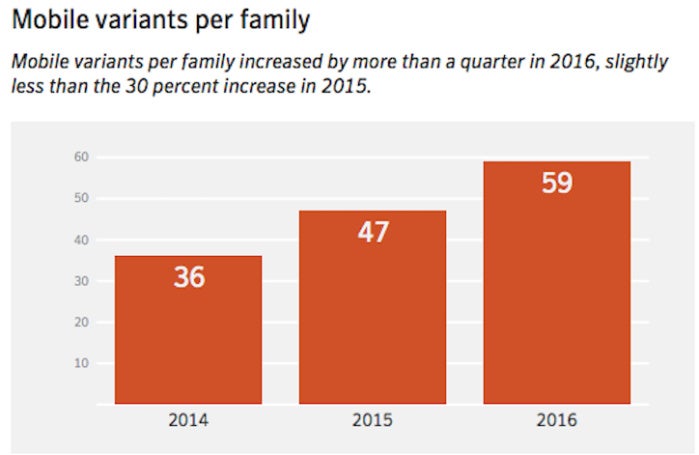
Variants are modifications hackers make to malware, and they can number in the thousands, overall. For example, last year there were 59 variants of 18 new malware families, which translates into more than 1,000 new mobile malware variants, according to Symantec. Mobile malware variants per family increased by more than a quarter in 2016, slightly less than the 30% increase in 2015.
iOS attacks occur, too
Those attacks included iOS.While rare, three zero-day vulnerabilities in iOS were exploited in targeted attacks to infect phones with Pegasus malware in 2016. Pegasus is a spy software that can take over an iPhone and access messages, calls, and emails.
The Pegasus malware can also gather information from apps, including Gmail, Facebook, Skype, and WhatsApp, according to Symantec.
The attack worked by sending a link to the victim through a text message. If the victim clicked on the link then the phone was jailbroken, Pegasus could be injected onto it and start spying.
The vulnerabilities that allowed the Pegasus attack to take place included one in the Safari WebKit that allowed an attacker to compromise the device if a user clicked on a link, an information leak in the OS kernel, and an issue where kernel memory corruption could lead to a jailbreak, Symantec said.
Just one mobile device infected with malware can cost an organization on average $9,485, according to a report issued last year by the Ponemon Institute. The potential financial consequences if a hacker compromises an employee’s mobile device to steal their credentials and access sensitive and confidential company data can be larger; it costs an average of $21,042 to investigate, contain and remediate damage from such an attack.
Android is making progress
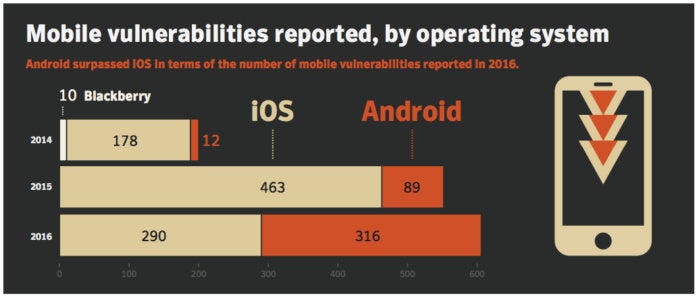
Among new malware attack vectors, Android continues to be the most targeted mobile platform, according to Symantec.A noteworthy change in 2016: Android surpassed iOS in terms of the number of mobile vulnerabilities reported, a stark contrast with previous years, "when iOS far outstripped Android in this area," Symantec said.
"This change may be partially attributed to continuing improvements in the security of the Android architecture and an ongoing interest by researchers in mobile platforms," the report noted.
"Following an explosive year in 2015," Symantec said, security improvements in Android's architecture "have made it increasingly difficult to infect mobile phones or to capitalize on successful infections."
William Stofega, IDC's program director for mobile phone research, agreed Google has made a concerted effort in recent years to take back control of its Android OS compared to its "wild west" early days, when anyone could change the source code.
 Symantec
Symantec"It's been implied that they're going to rebuild it and it won't be under public license, and they'll avoid disclosing source code," Stofega said. "It hasn't been implemented yet, but it would make it more difficult to break in.
"I still think there's been a lot of progress made -- not that it doesn't need additional progress," Stofega added.
Android smartphone and tablet manufacturers such as Samsung have also upped their security. For example, Samsung's Knox, a free containerization security app, enables greater separation between enterprise and personal data by creating a virtual Android environment within mobile devices -- complete with its own home screen -- as well as its own launcher, apps and widgets.
Knox creates a container so that only authorized personnel can access content within it. All files and data, such as email, contacts, and browsers are encrypted within the container.
Knox also allows end-users to securely add personal apps to the My Knox Container via Google Play. Once inside the container, the personal apps utilize the same security of Knox.
"A lot of this is about how you introduce something like Android into the enterprise," Stofega said.
A mobile malware strategy
As more companies adopt a "mobile first" business strategy, the most common solution to avoiding malware is relatively simple: keep the software on the devices regularly updated. Updating software to the latest platform helps address OS variants. Of course, while technically simple, all things are relative.For organizations that have a BYOD policy, getting users to update their mobile OS is, at best, a struggle, Gold said as "it's not their device."
Even for enterprises that issue mobile devices, updating software can be arduous and spur pushback from users. But it's critical to regularly issue patches and platform updates.
"I've talked to IT managers, and users often don't want to update their software. A lot of folks just don't keep to the schedule. But it's terribly important," Stofega said.
Companies should also avoid a "mobile" security strategy, Gold said.
"They should have a security strategy and mobile should be a part of it," he explained. "If you're trying to do something unique for mobile devices, it may not necessarily fit in with everything else you're doing in the company. Whereas, if you have an overarching security policy, then you can do all you want in mobile to fit in with that overarching strategy."
For example, companies are beginning to roll out encryption on mobile devices to protect corporate data, yet many they don't have it on their desktops. Conversely, if a company has two-factor authentication on PCs in order to access a corporate application, such as SAP, they should also have it on mobile devices, Gold said.
"Optimize security first, and then figure out what you can do on each device. In some cases you can't have equivalence. Just do the best you can," he said.
Gold, Stofega and Symantec recommend companies keep the software on corporate-issued mobile devices up to date, and issue frequent notices to employees using their own hardware to do the same. And it's important to remind workers to refrain from downloading apps from unfamiliar sites and install apps only from trusted sources.
Symantec also recommends that IT admins pay close attention to the permissions requested by mobile apps, as it can indicate malicious behavior.
Additionally, companies that do issue mobile devices to employees should ensure that Android devices are enhanced for corporate use. Google is addressing the needs of many business Android users by offering an enterprise-class upgrade known as Android at Work. The Android at Work mobile devices offer segmented workspaces and profiles to keep corporate and personal apps separate.
They also require companies to first deploy a set of enforcement tools on a mobile device, either through mobile device management or a wider-encompassing enterprise mobility management tool set, according to Gold.
Some new mobile malware has been identified as having rootkit capabilities, or modified OSes that can be used to gain administrative access to corporate systems. So enterprises should also install root detection software on mobile devices, or better yet, purchase mobile hardware already configured with root detection software.
"Essentially, this allows a way for any low-level code running the device to be pre-vetted so as to determine if it is genuine," Gold's report said. "It prevents the ability to root, or to substitute a corrupted OS that could then be used to boot the system."
Device manufacturers can also play a key role in making phones and tablets more secure. Some mobile vendors have been known to delay OS updates for months; that practice, according to Gold's report, should indicate to an enterprise that the vendor is an unacceptable hardware supplier.
Lastly, while adding security feature to mobile devices is recommended, it's not as useful as simply stick to good practices. Educating employees about best practices, such as not downloading apps they've not vetted or opening unexpected attachments in messages, is crucial.
"A lot of this is about getting users on your side," Gold said. "Dialogue with them and educate them on why security is necessary. There are a lot of practices users do that they shouldn't, but they simply don't know any better."



Thanks mob2web for providing us such a important article!
ReplyDeletePls add a post on is omegle safe?